Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Descrição
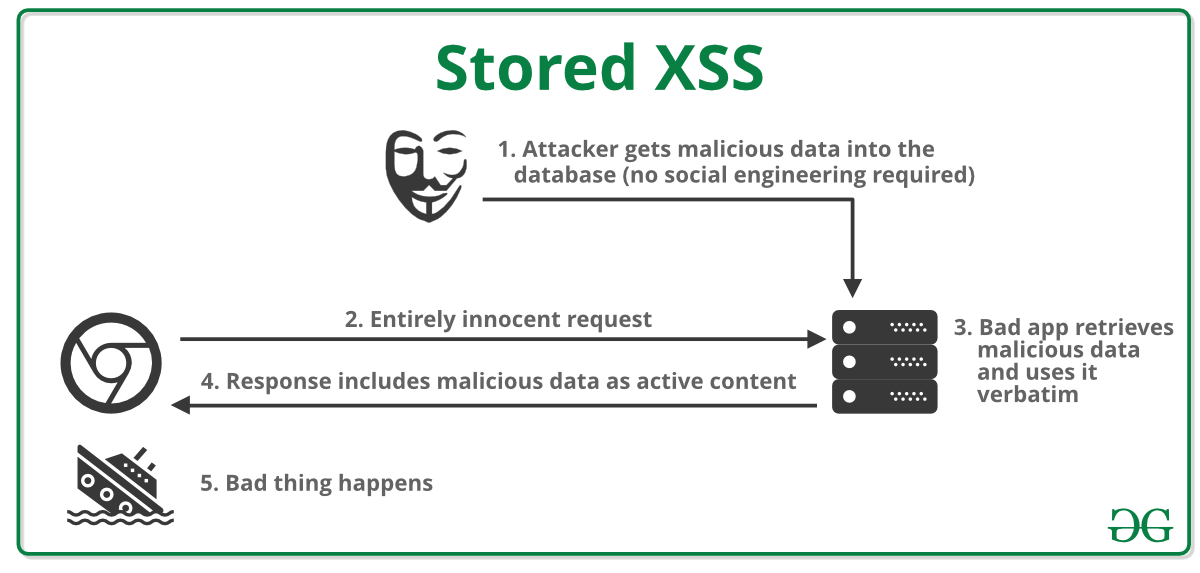
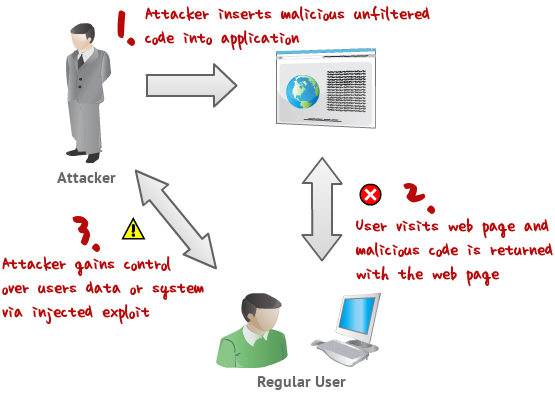
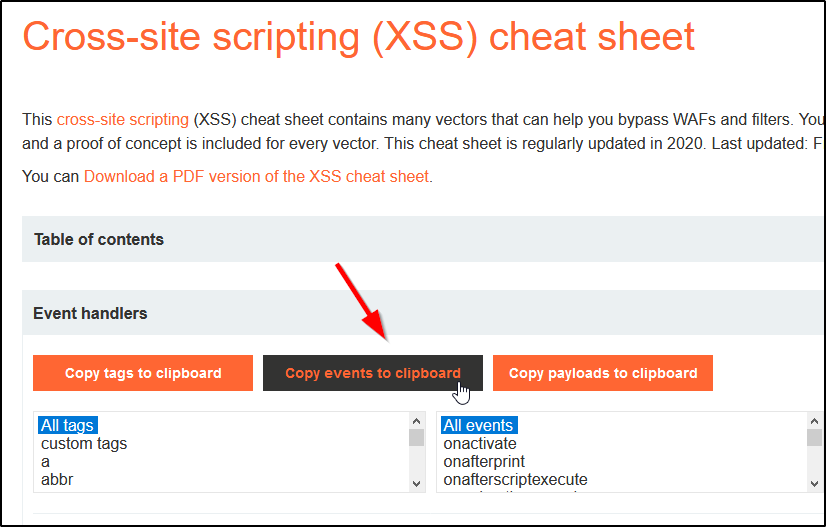
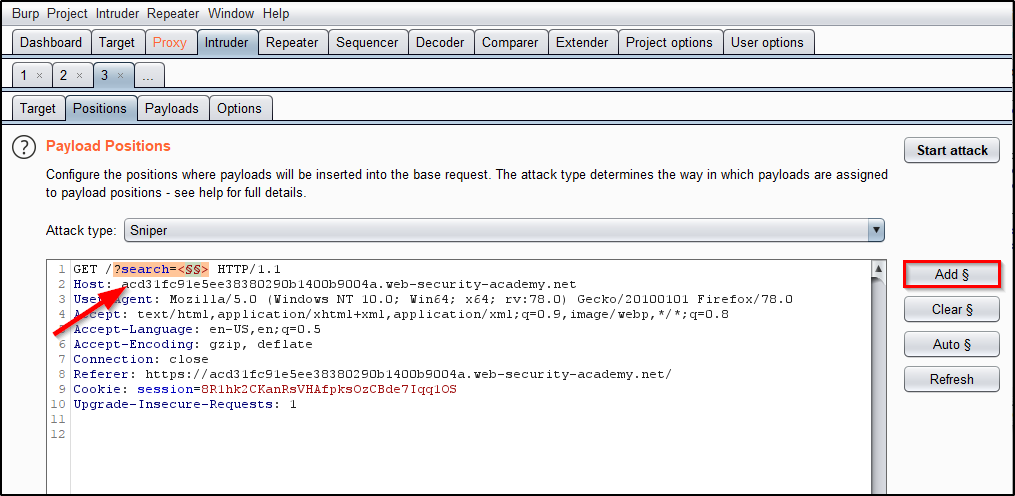
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…
Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Mastering XSS: A Comprehensive Guide for Bug Bounty Hunters, by Security Lit Limited
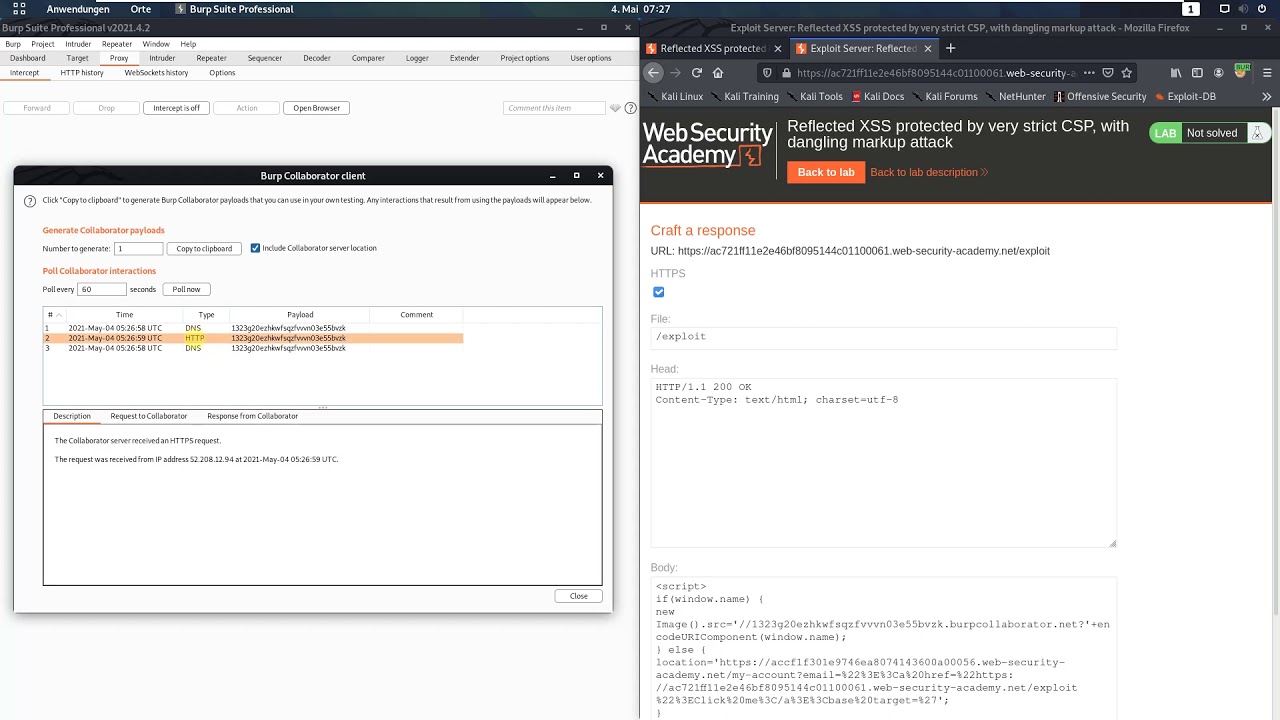
Reflected XSS protected by very strict CSP, with dangling markup attack (Video solution, Audio)
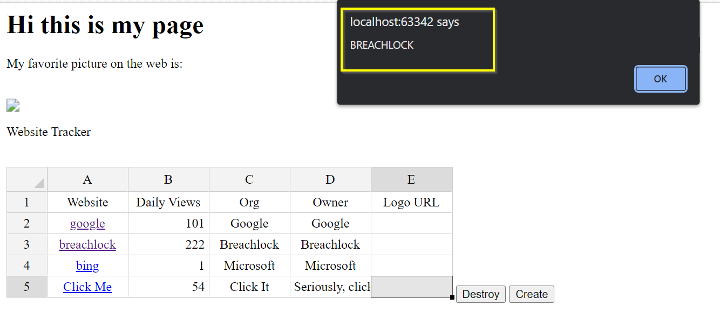
How to Fix XSS Vulnerabilities on Web App Links - BreachLock
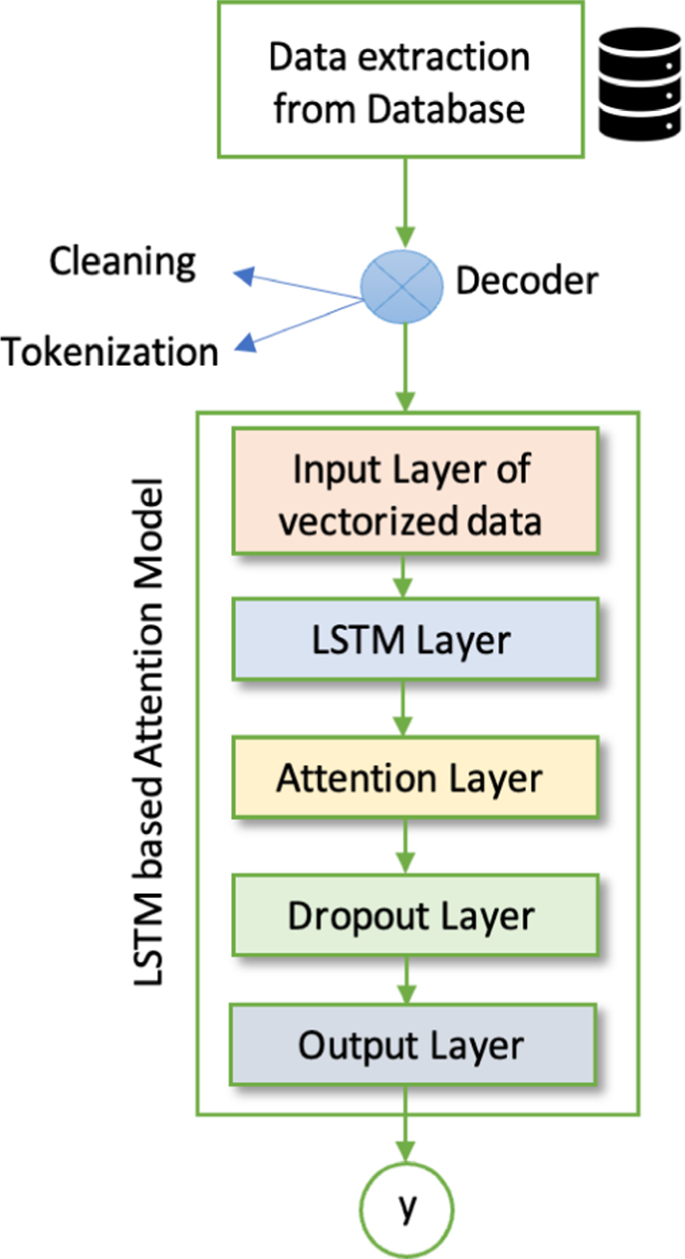
Detection of cross-site scripting (XSS) attacks using machine learning techniques: a review

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Bypassing Signature-Based XSS Filters: Modifying HTML - PortSwigger

XSS‐immune: a Google chrome extension‐based XSS defensive framework for contemporary platforms of web applications - Gupta - 2016 - Security and Communication Networks - Wiley Online Library

GAXSS: Effective Payload Generation Method to Detect XSS Vulnerabilities Based on Genetic Algorithm

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Is cross-site scripting still a security threat? - Quora
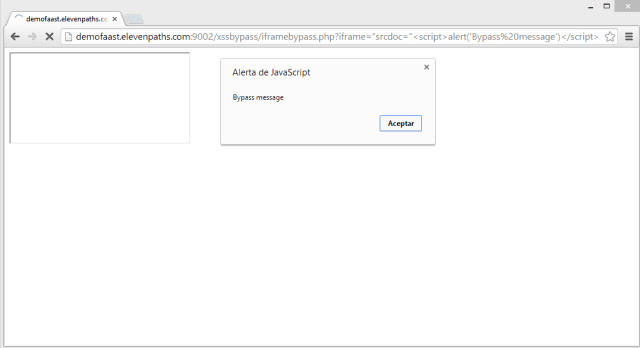
How to bypass antiXSS filter in Chrome and Safari (discovered by ElevenPaths) - Think Big
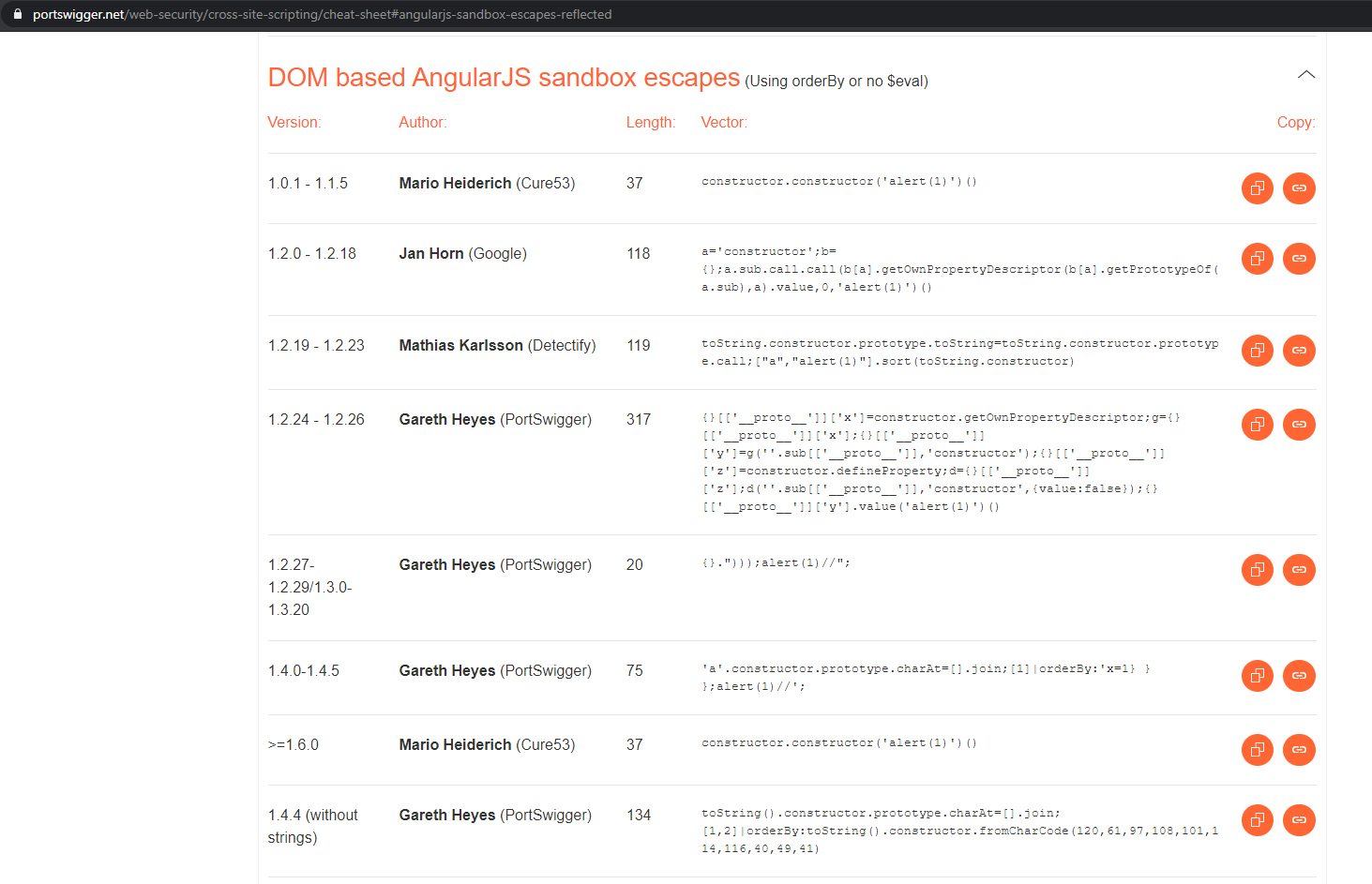
Attempting to Bypass the AngularJS Sandbox from a DOM-Based Context in versions 1.5.9-1.5.11 (Part 1) - Anvil Secure
de
por adulto (o preço varia de acordo com o tamanho do grupo)