Malware analysis Malicious activity
Por um escritor misterioso
Descrição

What to Include in a Malware Analysis Report

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen
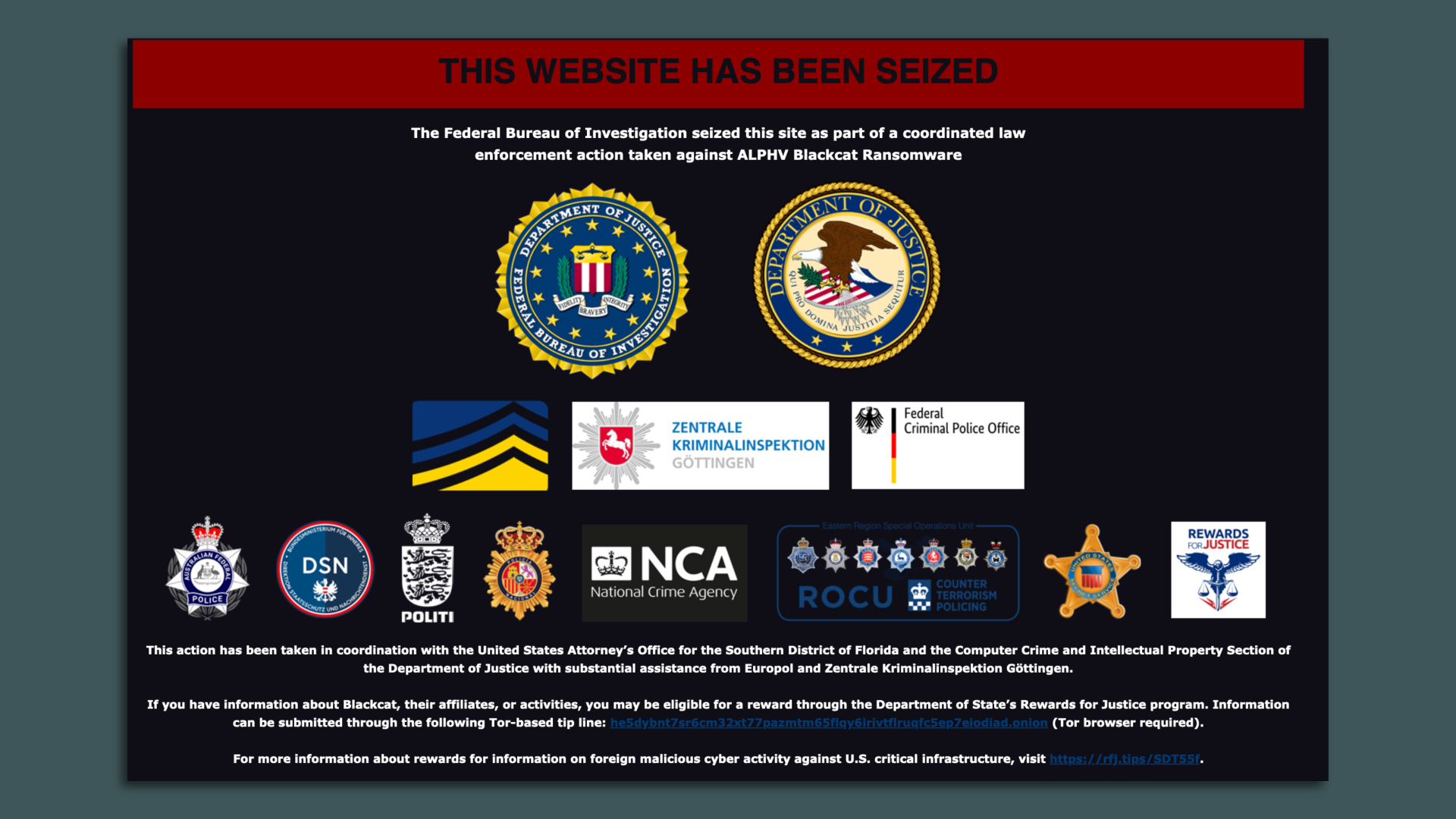
U.S. law enforcement seizes BlackCat ransomware site, distributes decryption key

Malware Analysis: Protecting Your Network from Cyber Attacks

Cybersecurity Search Engine

Malware analysis Program_Install_and_Uninstall Malicious activity

MetaDefender Cloud Advanced threat prevention and detection

How to build a malware analysis sandbox with Elastic Security
Lab 6-1 Solutions - Practical Malware Analysis [Book]

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus
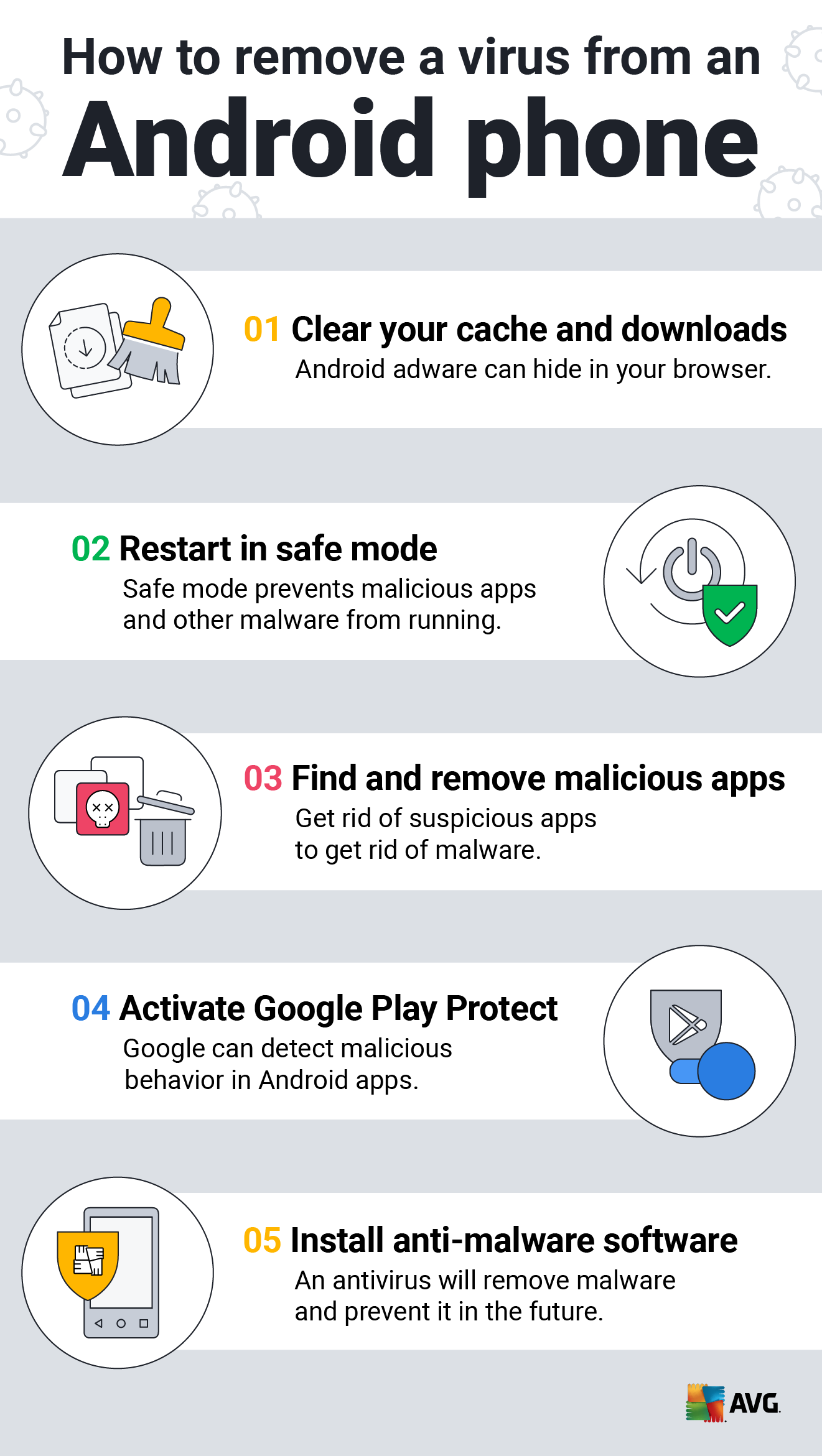
How to Clean an Android or iPhone from Viruses for Free

What is Malware? Definition, Types, Prevention - TechTarget
Interactive Online Malware Sandbox
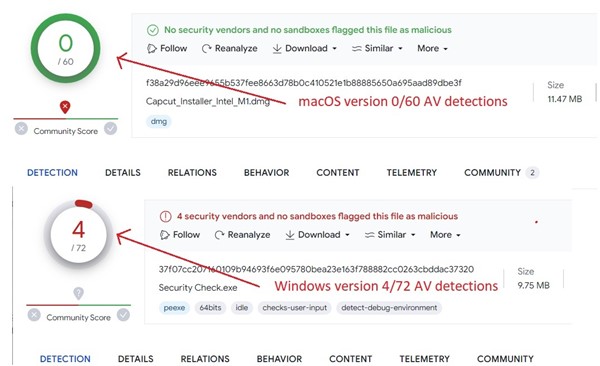
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows
de
por adulto (o preço varia de acordo com o tamanho do grupo)







