Create a malicious Trojan application for Androids using Kwetza, by David Artykov, Purple Team
Por um escritor misterioso
Descrição
Infecting Android apps is a perfect way to see how malicious activities in the wild, such as malware and practical jokes, affect people. This not only gives you access to user computers, but it also…

Angry IP Scanner for your network, by David Artykov, Purple Team
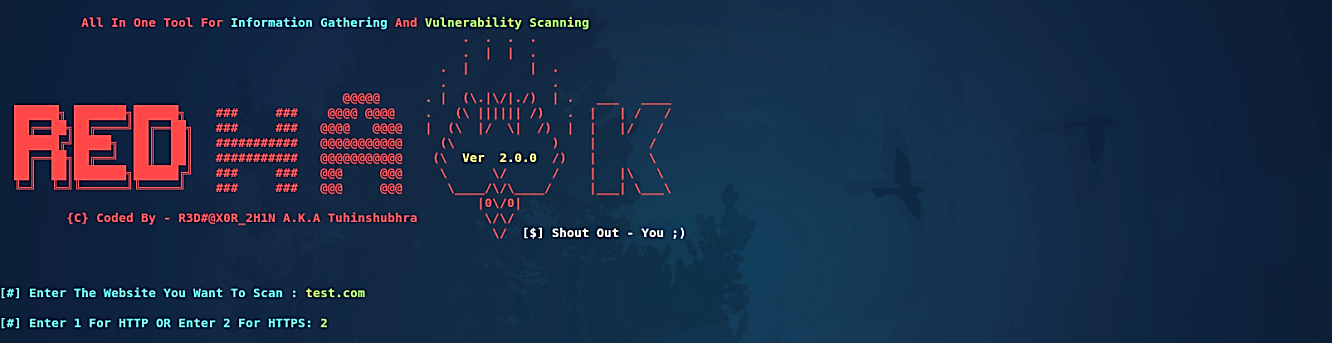
Red Hawk — web application scanner for recon, by David Artykov, Purple Team

Android Debug Bridge (ADB) exploitation (privilege escalation), by David Artykov, Purple Team

Kwetza Github Get File - Colaboratory

Defend the Web” write-up (HTTP Method / Intro — HTTP POST exploitation and bypassing CSRF token protection), by David Artykov, Purple Team
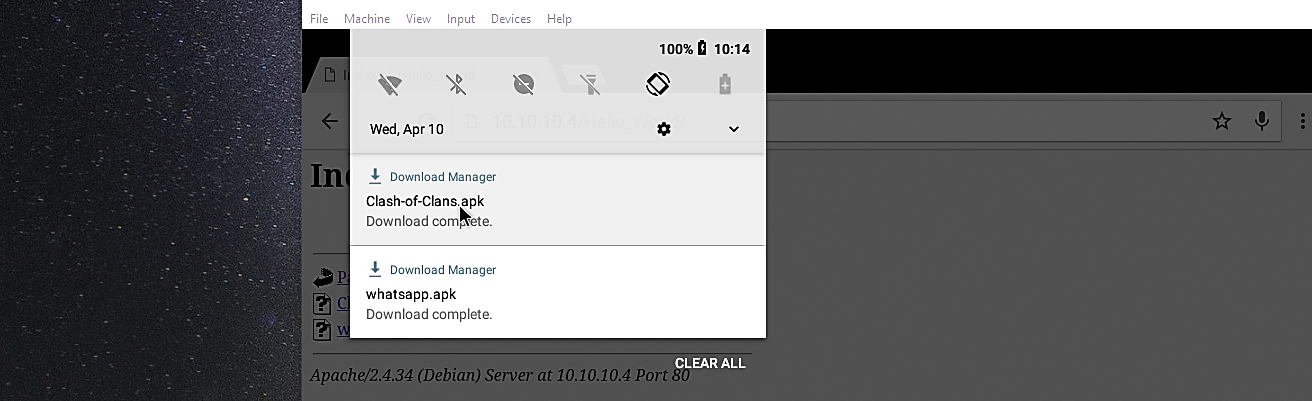
Create a malicious Trojan application for Androids using Kwetza, by David Artykov, Purple Team

Red Hawk — web application scanner for recon, by David Artykov, Purple Team

Email address harvesting. Email harvesting is the process of…, by David Artykov, Purple Team

Programming – Purple Team – Medium

Defend the Web” write-up (Intro 7— robots.txt data leak vulnerability), by David Artykov, Purple Team
de
por adulto (o preço varia de acordo com o tamanho do grupo)